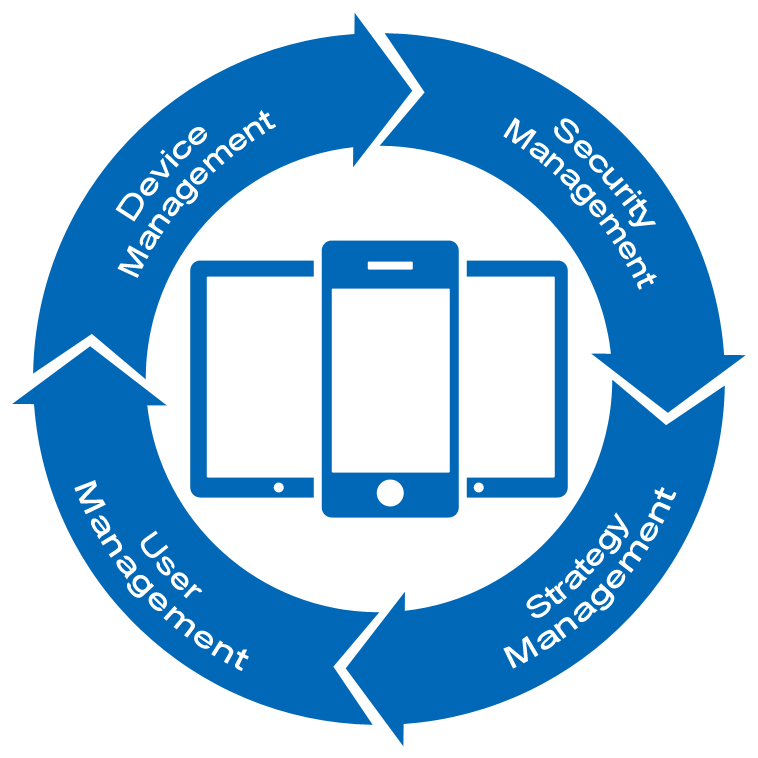
Device management
Manage the mobile devices connected to BestEMM, get remotely device hardware info, software info, and security info. Monitor the running state of devices in real time.
Asset management
Manage the tangible assets and intangible assets of enterprise mobile devices and display graphically to prevent the loss of corporate assets.
Security management
Monitor the jailbreaking, ROOT status of mobile devices, virus infections, SIM card replacement, the security situation of illegal programs in real time. |
 |
Log management
Make unified management of system logs, user logs, device logs, app logs, operation logs, display them graphically, and analyze all the data produced by the system in detail to prevent the potential safety hazard.
Strategy management
Make multiple combinations of strategy management for the mobile devices and configure remotely the functional authority and network environment of the mobile devices.
Authority management
Manage the access of mobile devices connected to BestEMM, limit using phones, messages, cameras, WiFi, Bluetooth, GPS, etc.
User management
Adopt the user management system based on roles and make full lifecycle management of users. The users can bind with multiple devices, and integrate seamlessly with the original user system of enterprise.
Wipe remote devices
Wipe the data and files of remote mobile devices through the function of wiping mobile devices to prevent divulgence of enterprise data files because of the loss of mobile devices. |